What is Medical Device Cybersecurity?
Cybersecurity for medical devices is vital for protecting both the data and lives of patients, as well as safeguarding medical institutions from ransomware attacks. With the evolution of medical devices and their connectivity, cyberthreats have continued to evolve in tandem, creating new risks.
Why is Connected Medical Device Security so Important?
The risks in medical device cybersecurity are multifaceted, emphasising the need for up-to-date certifications and standards, as well as undergoing thorough cybersecurity evaluations. Effective risk management involves enhancing life cycle processes to identify vulnerabilities and strengthen security through rigorous penetration testing.
Cybersecurity Risks and Requirements for Medical Devices
- Regulatory requirements:
Medical devices are subject to stringent regulations by bodies such as the FDA in the United States, the EMA in Europe, NMPA in China, and other regional regulatory agencies. These regulations require adherence to specific cybersecurity standards and guidelines to ensure devices are safe from hacking and other cyber threats. Non-compliance can result in severe penalties, recalls, or bans. - Patient safety:
Cybersecurity flaws in medical devices can directly jeopardise patient safety. If a device such as a pacemaker or insulin pump is breached, it could malfunction, delivering incorrect treatment doses or failing at critical moments. - Privacy and Disruptions:
Since medical devices often store and transmit sensitive health information, a security breach can expose personal health records, leading to identity theft and loss of patient confidentiality. This is a typical risk in ransomware attacks, where malicious actors encrypt critical data and demand a ransom to unlock it. Such attacks not only compromise patient privacy but also disrupt the essential operations of healthcare systems, underscoring the critical need for robust cybersecurity measures.
Cybersecurity Medical Devices Standards and Guidelines
Given the risks involved, medical device cybersecurity is tested against stringent international and national standards. Regulatory bodies around the world have published guidelines concerning the regulation of medical device cybersecurity and outline the tests that they need to undergo to reach markets. At Applus+ Laboratories, we can support you with the following standards:
- EU MDR / MDCG 2019-16 EU Guidance on Medical Device Cybersecurity: Ensuring the integrity and confidentiality of medical device data across the European market.
- USA / FDA Guidance on Cybersecurity in Medical Devices - Quality System Considerations and Content of Premarket Submissions (June 2025): Guidelines for incorporating cybersecurity measures from design to deployment within the U.S. regulatory framework.
- IEC TR 60601-4-5 Standard for Medical Device Cybersecurity: A technical roadmap for implementing global cybersecurity standards in medical devices.
- IEC 81001-5-1 Standard for Health Software and Heath IT Systems Security Activities in the Product Life Cycle: Strategies for maintaining cybersecurity throughout the device's operational life, applicable worldwide.
- IEEE 2621 is a family of standards used in the IEEE Medical Device Cybersecurity Certification Program. Recognized by the FDA, these standards are designed to align with national cybersecurity strategies issued by the U.S. Government. Applus+ serves as an approved testing laboratory for IEEE 2621. Devices that achieve certification are listed in the IEEE Medical Device Registry and may display the IEEE certification mark to distinguish themselves from competitors.
Do you need to comply with the EU MDR regulation and FDA cybersecurity requirements?
If your product meets any of the following statements, it should undergo a cybersecurity testing process:
- Supports software or firmware downloads (e.g., updates or patching).
- Provides access to cloud storage or cloud services.
- May have unused ports for network connectivity.
- Utilizes any type of wireless communication (e.g., Bluetooth, Wi-Fi, cellular, RF, inductive).
- Can interface with other devices or systems.
- Contains a USB port or physical media access (e.g., memory card, IAG).
In the EU, market access for medical devices is regulated by the EU Medical Devices Regulation (MDR), which became mandatory for new products in 2021, replacing the old Medical Device Directive (MDD). The MDR includes more than just security-related requirements.
In the US, the FDA regulates market access for medical devices. Manufacturers must undergo a Premarket Submission process before selling products. The FDA reviews this submission and grants approval for market entry.
Both the FDA and EU MDR regulations have similar requirements. Key expectations from regulators include:
- Comprehensive risk management documentation, including threat analysis (assets, vulnerabilities, threats) and "state of the art" security controls to mitigate risks.
- Security guidance and labelling documentation, clarifying the security risks and expected configurations, hardening, and mitigation.
- Evidence of security testing, such as code reviews and vulnerability scans.
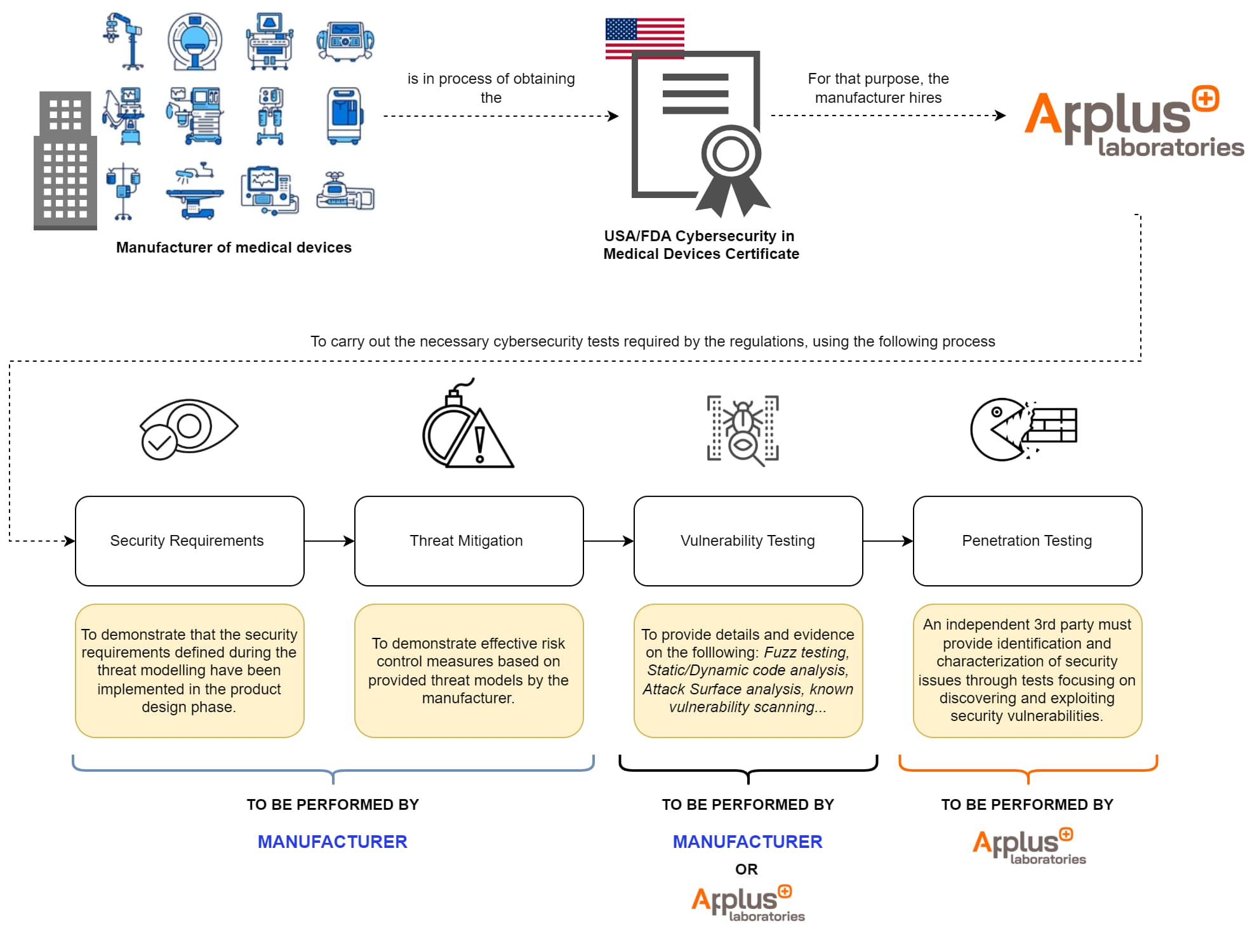
FDA Cybersecurity Testing
The cybersecurity testing required by the FDA is designed to ensure medical devices security and effectiveness. This includes various phases:
- Security Requirements (to be performed by the manufacturer):
- The manufacturer must provide evidence that during the design phase of their product, the security requirements defined during the threat modelling have been implemented.
- The manufacturer must provide evidence on how these security requirements have been correctly implemented, and an analysis and justification of boundary assumptions.
- Threat Mitigation (to be performed by the manufacturer):
- The manufacturer must provide evidence demonstrating effective risk control measures based on provided threat models.
- The manufacturer must provide evidence on how to verify that each cybersecurity risk control is adequate (e.g. the effectiveness of security in enforcing the specified security policy, performance under peak traffic conditions, stability, and reliability).
- Vulnerability Testing (to be performed by the manufacturer or independent 3rd party):
- The manufacturer or a third party must provide details and evidence of the following testing and analyses:
- Robustness.
- Fuzz testing.
- Static and dynamic code analysis.
- Attack surface analysis.
- Closed box testing of known vulnerability scanning.
- Software composition analysis of binary executable files.
- The manufacturer or a third party must provide details and evidence of the following testing and analyses:
- Penetration Testing (to be performed by an independent 3rd party):
- An independent 3rd party must provide identification and characterization of security issues through tests focusing on discovering and exploiting security vulnerabilities.
- Penetration test reports should include the following elements:
- Independence and technical expertise of testers.
- Scope and duration of tests.
- Testing methods.
- Results.
- Findings observations.
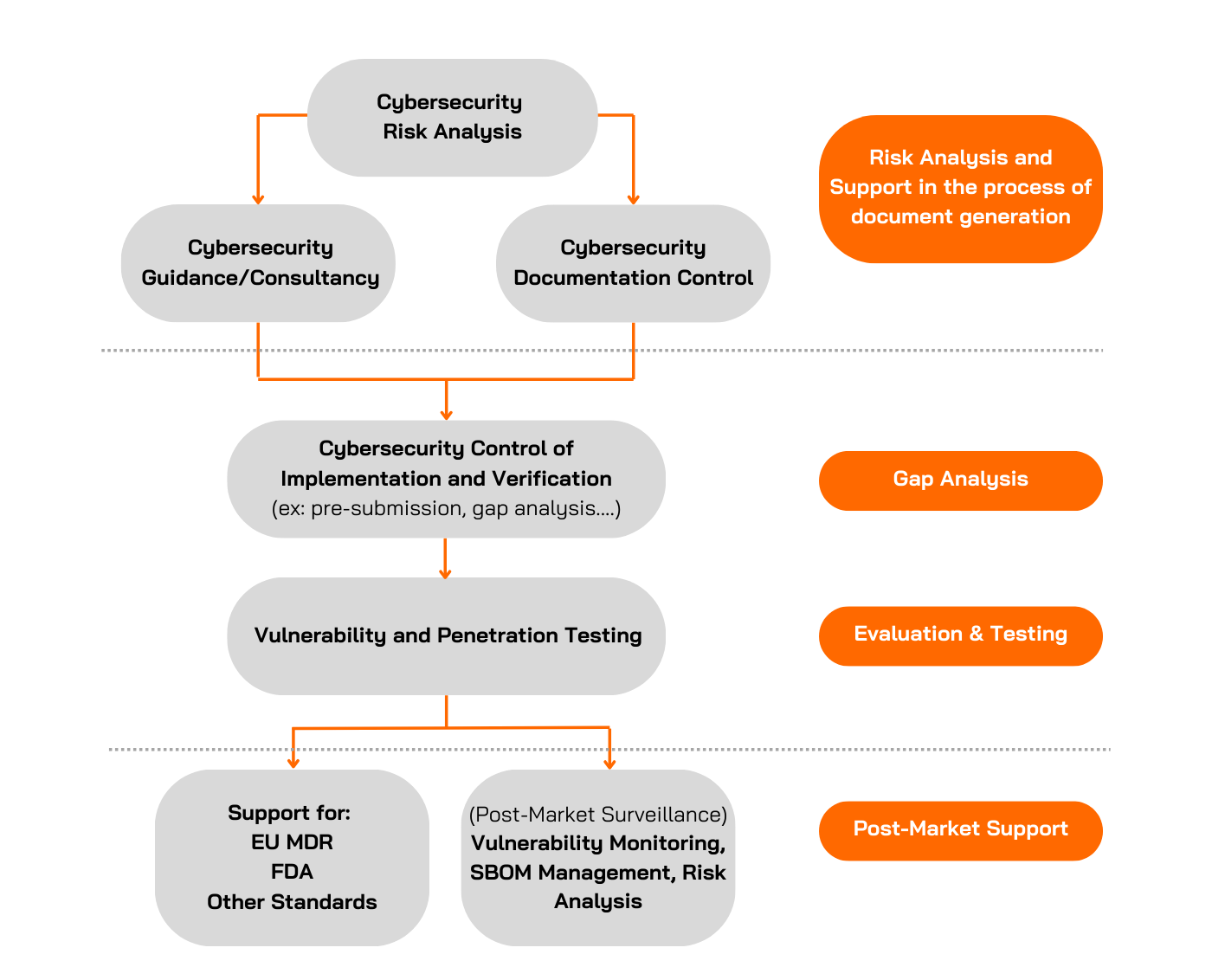
Medical Device for Cybersecurity Certification Process
Why Choose Applus+ Laboratories for Cybersecurity for Medical Devices?
Applus+ Laboratories offers comprehensive cybersecurity testing services for evaluating medical devices. We have many years of experience conducting cybersecurity evaluations and carrying out penetration tests on all kinds of Targets of Evaluation (TOEs). We can support you throughout the entire process of complying with both EU MDR and FDA standards.
Penetration Testing
Applus+ Laboratories offers extensive penetration testing services to assess the resilience of systems against attacks and unauthorised access. By performing cyberattack simulations, we evaluate vulnerabilities in medical devices across various components:

On Hardware
State-of-the-art attacks and ad-hoc tools made by lab experts:- Reverse Engineering
- Design Review
- Logical Attacks
- Storage extraction and external analysis

On Software & Firmware
Strong background in embedded systems, secure boot, TEE and white box crypto:- Binary Reverse Engineering
- Static Attacks
- Source Code Audits
- Debugging
- Fuzzing
- Dynamic Tamper / Hooking

On Communication Protocols
For IP stack protocols, industrial systems and proprietary protocols:- All layer attack (OSI Model) including customised HW to stimulate at lower layers (wired & wireless protocols)
- Fuzzing
Our expertise in cybersecurity further enhances the security measures we recommend. Penetration testing activities conducted in our expert lab not only help to strengthen product cyber resilience but also serve as proof of compliance with cybersecurity requirements mandated by regulatory bodies worldwide, such as the FDA in the USA.
Gap Analysis
Our teams can also support manufacturers worldwide by verifying if their products comply with specific standards or guidelines requested by regulatory bodies.
At Applus+ Laboratories, we review the documentation generated by the manufacturer to determine if it meets the specific standard, identifying any gaps or potential challenges. During this phase, the Applus+ Laboratories team will analyse, guide, and support the manufacturer in preparing the required documentation before submission to the regulatory body.
Example: For FDA Cybersecurity Testing, the Applus+ Laboratories team offers an optional service to review the manufacturer's documentation prior to premarket submission, focusing on 1) Security Requirements, 2) Threat Mitigation and 3) Vulnerability Testing, analysing, among other things, the defined security requirements and whether they align with the security issues identified in the threat modelling, as well as the defined hypotheses, the suitability of the vulnerability testing, etc.
Project and Products Experience
- Picture Archiving and Communication Systems
- Surgery Planning Software
- Surgery Navigation System Software
- Radiation Therapy Planning System
- Pelvic Floor Assessment Training Software
- IVD Data Interpretation Software
- Mobile APPs of Medical Device
- Amongst others
- Medical Imaging Systems(X-Ray, CT, MR etc.)
- Automated External Defibrillator (AED)
- Endoscopic Video System
- Ambulatory Electroencephalogram (EEG) Machine
- Electrocardiogram (ECG) Machine
- Laser Scalpel
- Laser Therapy Device
- Amongst Others